Unlocking The Power Of IoT SSH Access On AWS: A Must-Know Guide For Tech Enthusiasts!
Ever wondered how IoT SSH access on AWS can transform the way you manage devices remotely? Well, buckle up because we're diving deep into this tech marvel! IoT SSH access AWS has become a game-changer for businesses looking to enhance their device management capabilities. Whether you're a tech newbie or a seasoned pro, understanding this system is crucial for staying ahead in the digital race.
In today's fast-paced world, connectivity is king. And when it comes to managing IoT devices, having secure and seamless access is not just a perk—it's a necessity. AWS has stepped up its game by offering robust solutions for IoT SSH access, ensuring your devices are always within reach. From smart homes to industrial automation, the possibilities are endless.
But why should you care? Because mastering IoT SSH access AWS can significantly boost your operational efficiency, save costs, and improve security. So, whether you're securing your devices or scaling your business, this guide will walk you through everything you need to know. Let's get started!
Read also:Abby Berner Nudes Separating Facts From Fiction And Understanding The Bigger Picture
What is IoT SSH Access AWS?
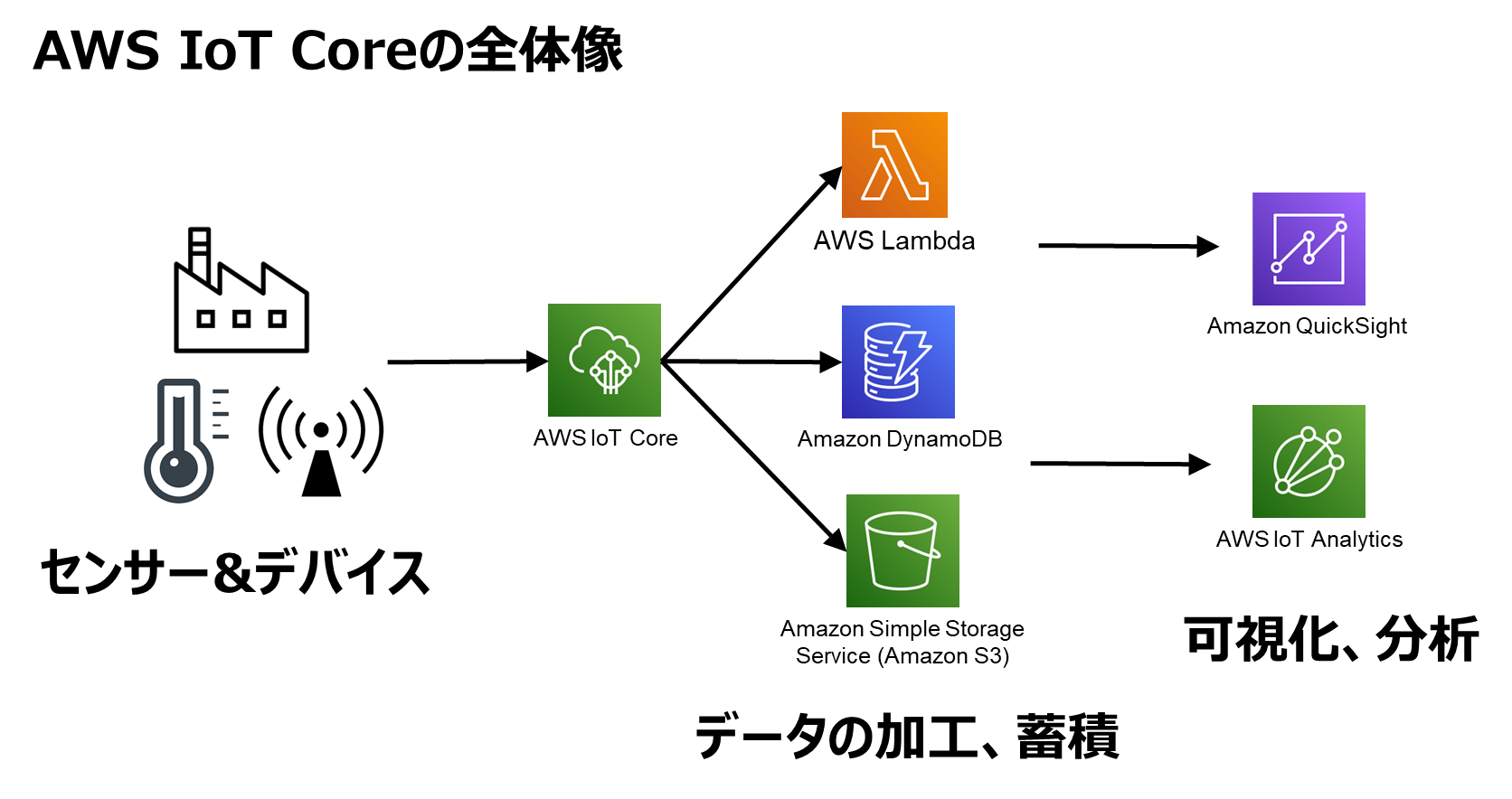
IoT SSH access AWS refers to the secure method of remotely accessing Internet of Things (IoT) devices hosted on Amazon Web Services (AWS). Think of it as a digital key that lets you unlock and control your devices from anywhere in the world. SSH, or Secure Shell, is a cryptographic network protocol that ensures secure communication between devices, even over unsecured networks.
By leveraging AWS's vast infrastructure, businesses can manage their IoT devices with ease, ensuring they remain secure and functional. This system is particularly useful for organizations dealing with a large number of devices spread across different locations. With IoT SSH access AWS, you can perform tasks like troubleshooting, updating firmware, and monitoring performance—all without being physically present.
Why Choose AWS for IoT SSH Access?
Here are some compelling reasons why AWS stands out for IoT SSH access:
- Scalability: AWS offers unparalleled scalability, allowing you to manage thousands of devices effortlessly.
- Security: With advanced encryption and authentication protocols, AWS ensures your devices are protected from unauthorized access.
- Integration: AWS seamlessly integrates with other services, making it easier to build comprehensive IoT solutions.
- Cost-Effective: Pay only for what you use, making it an affordable option for businesses of all sizes.
Setting Up IoT SSH Access AWS
Setting up IoT SSH access AWS might seem daunting at first, but with the right steps, it's a breeze. Here's a quick guide to get you started:
Step 1: Create an AWS Account
If you haven't already, sign up for an AWS account. It's free to start, and you can explore the platform without any commitments.
Step 2: Set Up an IoT Core
Once your account is ready, head over to the AWS Management Console and set up an IoT Core. This will serve as the backbone of your IoT ecosystem, enabling secure communication between devices.
Read also:Bollyflixindin The Ultimate Hub For Bollywood Enthusiasts
Step 3: Configure SSH Access
Next, configure SSH access for your devices. This involves setting up security groups, key pairs, and other necessary configurations to ensure secure access.
Benefits of IoT SSH Access AWS
The benefits of using IoT SSH access AWS are numerous. Let's break them down:
- Enhanced Security: With built-in encryption and authentication, your devices are protected from cyber threats.
- Remote Management: Manage your devices from anywhere, at any time, without compromising security.
- Cost Efficiency: Reduce operational costs by automating tasks and minimizing downtime.
- Scalability: Easily scale your operations as your business grows, without worrying about infrastructure limitations.
Common Challenges and Solutions
While IoT SSH access AWS offers numerous advantages, it's not without its challenges. Here are some common issues and how to overcome them:
Challenge 1: Security Vulnerabilities
Solution: Implement strong authentication mechanisms, regularly update firmware, and monitor your devices for suspicious activity.
Challenge 2: Connectivity Issues
Solution: Ensure your devices are connected to a stable network and configure failover mechanisms to handle disruptions.
Challenge 3: Scalability Concerns
Solution: Use AWS's auto-scaling features to handle spikes in traffic and ensure your system can accommodate future growth.
Best Practices for IoT SSH Access AWS
To make the most of IoT SSH access AWS, here are some best practices to follow:
- Regularly update your devices and software to patch vulnerabilities.
- Implement role-based access control to restrict access to sensitive data.
- Monitor your devices in real-time to detect and respond to threats quickly.
- Document your processes and configurations for future reference.
Case Studies: Real-World Applications
Let's take a look at some real-world applications of IoT SSH access AWS:
Case Study 1: Smart Home Automation
A leading smart home provider used IoT SSH access AWS to manage thousands of devices across multiple locations. By leveraging AWS's scalability and security features, they were able to provide seamless and secure access to their customers.
Case Study 2: Industrial Automation
A manufacturing company implemented IoT SSH access AWS to monitor and control their production line remotely. This resulted in significant cost savings and improved operational efficiency.
Future Trends in IoT SSH Access AWS
The future of IoT SSH access AWS looks promising, with several trends emerging:
- Increased adoption of AI and machine learning for predictive maintenance.
- Enhanced security measures to combat rising cyber threats.
- Integration with emerging technologies like 5G for faster and more reliable communication.
Conclusion
In conclusion, IoT SSH access AWS is a powerful tool that can revolutionize the way you manage your IoT devices. By understanding its capabilities and following best practices, you can unlock its full potential and stay ahead in the tech game. So, what are you waiting for? Dive in and explore the endless possibilities!
And hey, don't forget to share your thoughts and experiences in the comments below. Let's keep the conversation going and help each other grow. Cheers!
Table of Contents
- What is IoT SSH Access AWS?
- Why Choose AWS for IoT SSH Access?
- Setting Up IoT SSH Access AWS
- Benefits of IoT SSH Access AWS
- Common Challenges and Solutions
- Best Practices for IoT SSH Access AWS
- Case Studies: Real-World Applications
- Future Trends in IoT SSH Access AWS
- Conclusion