RemoteIoT SSH AWS Example: Your Ultimate Guide To Secure Remote Access
Hey there, tech enthusiasts! Let’s talk about something super cool that’s taking the tech world by storm—RemoteIoT SSH AWS Example. Imagine being able to securely connect to your IoT devices from anywhere in the world using AWS services. Sounds awesome, right? This isn’t just a buzzword; it’s a game-changer for businesses and individuals alike who want to manage their IoT infrastructure remotely without compromising on security. So, buckle up, because we’re diving deep into this topic and giving you all the juicy details you need to know.
In today’s fast-paced digital era, the ability to remotely access and manage IoT devices has become essential. With the rise of cloud computing and the Internet of Things, leveraging AWS for secure remote access is no longer a luxury—it’s a necessity. RemoteIoT SSH AWS Example is your ticket to mastering this process, ensuring your devices are always under control, no matter where you are.
But why should you care? Well, security breaches can cost businesses millions of dollars, and downtime can ruin reputations. By understanding how RemoteIoT SSH works on AWS, you’re not just staying ahead of the curve—you’re safeguarding your operations. Let’s get started!
Read also:Unveiling Mydesi Net Your Ultimate Guide To Everything You Need To Know
Here’s a quick roadmap to help you navigate this article:
- What is RemoteIoT SSH AWS Example?
- Why Use AWS for RemoteIoT SSH?
- A Quick Background on IoT and SSH
- The Setup Process Explained
- Tools You’ll Need
- Security Best Practices
- Troubleshooting Tips
- Real-World Examples
- Cost Considerations
- Future Trends in RemoteIoT SSH
What is RemoteIoT SSH AWS Example?
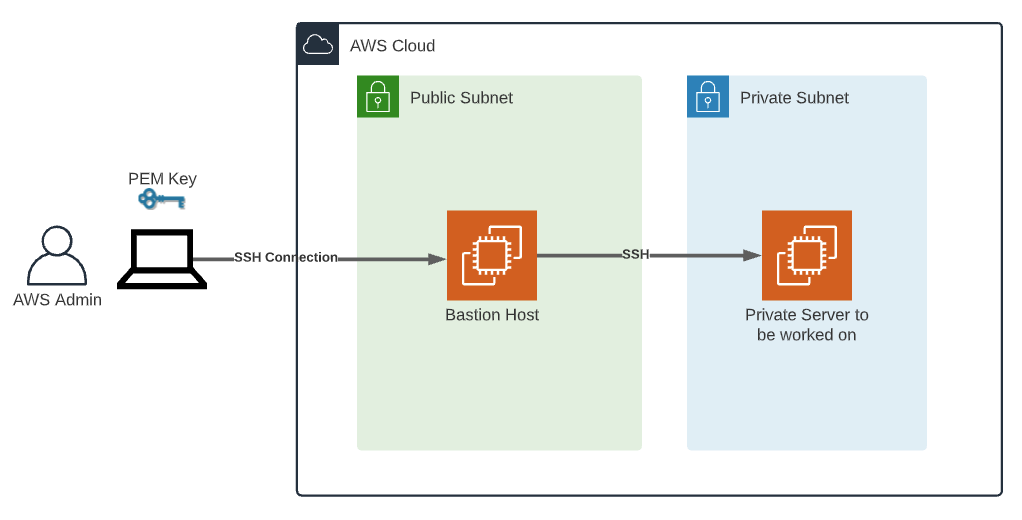
Alright, let’s break it down. RemoteIoT SSH AWS Example refers to the process of setting up secure remote access to IoT devices using SSH (Secure Shell) over Amazon Web Services (AWS). Think of it as a virtual bridge that connects your devices to the cloud, allowing you to monitor, manage, and troubleshoot them from anywhere.
SSH itself is a cryptographic protocol designed to provide secure communication over unsecured networks. When paired with AWS, it becomes a powerhouse for managing IoT devices. AWS offers a range of services like EC2 instances, S3 buckets, and Lambda functions that can be integrated into your IoT setup, making it scalable and efficient.
Why SSH is Crucial for RemoteIoT
SSH isn’t just about logging in remotely; it’s about ensuring that your data remains private and protected. With RemoteIoT SSH AWS Example, you can:
- Encrypt all communication between your device and the cloud.
- Authenticate users securely to prevent unauthorized access.
- Automate tasks and scripts to streamline your workflow.
Why Use AWS for RemoteIoT SSH?
Now, you might be wondering why AWS is the go-to platform for RemoteIoT SSH setups. The answer is simple: AWS offers unparalleled scalability, flexibility, and security. Here’s why it stands out:
First off, AWS provides a robust infrastructure that can handle thousands of IoT devices simultaneously. Whether you’re managing a small fleet of sensors or a massive network of connected devices, AWS has got you covered. Plus, its global network of data centers ensures low latency and high availability, which is crucial for real-time monitoring and control.
Read also:Malygon Nude The Untold Story Thats Capturing Everyones Attention
Key Benefits of AWS for RemoteIoT
- Scalability: Easily scale your IoT infrastructure as your needs grow.
- Security: AWS offers advanced security features, including encryption, IAM roles, and VPCs.
- Cost-Effective: Pay only for what you use, making it budget-friendly for businesses of all sizes.
A Quick Background on IoT and SSH
Before we dive deeper into RemoteIoT SSH AWS Example, let’s take a step back and understand the origins of IoT and SSH. IoT, or the Internet of Things, refers to the network of physical devices embedded with sensors, software, and connectivity, enabling them to exchange data. SSH, on the other hand, was developed in the late 1990s as a secure alternative to Telnet, providing encrypted communication over insecure networks.
Data Table:
| Technology | Description | Year Introduced |
|---|---|---|
| IoT | Network of connected devices | Early 2000s |
| SSH | Cryptographic protocol for secure communication | 1995 |
The Setup Process Explained
Setting up RemoteIoT SSH AWS Example might seem intimidating at first, but with the right guidance, it’s totally doable. Here’s a step-by-step breakdown:
- Create an AWS Account: Sign up for an AWS account if you haven’t already.
- Launch an EC2 Instance: Choose an instance type that suits your needs and launch it.
- Configure Security Groups: Set up security groups to allow SSH access.
- Connect to Your Device: Use an SSH client to connect to your IoT device via the EC2 instance.
Common Pitfalls to Avoid
While setting up, keep an eye out for these common mistakes:
- Forgetting to open the necessary ports in your security group.
- Not securing your SSH keys properly.
- Ignoring best practices for password management.
Tools You’ll Need
To successfully implement RemoteIoT SSH AWS Example, you’ll need a few essential tools:
- AWS Management Console: For managing your AWS resources.
- SSH Client: Tools like PuTTY or OpenSSH for establishing secure connections.
- IoT Device: The device you want to manage remotely.
Security Best Practices
Security should always be at the forefront of your mind when setting up RemoteIoT SSH AWS Example. Here are some tips to keep your setup secure:
Use strong, unique passwords for all your accounts. Enable multi-factor authentication (MFA) wherever possible. Regularly update your software and firmware to patch vulnerabilities. And most importantly, monitor your logs for any suspicious activity.
Encryption Protocols
When it comes to encryption, AWS supports a variety of protocols, including AES, RSA, and ECC. Make sure you’re using the latest and strongest encryption methods available to protect your data.
Troubleshooting Tips
Even the best-laid plans can go awry sometimes. If you run into issues with your RemoteIoT SSH AWS Example setup, here’s what you can do:
- Check your security group settings to ensure the right ports are open.
- Verify that your SSH keys are correctly configured.
- Consult AWS documentation or reach out to their support team for assistance.
Real-World Examples
Let’s look at some real-world examples of companies using RemoteIoT SSH AWS Example:
One company, for instance, uses this setup to monitor environmental sensors in remote locations. By leveraging AWS, they can collect data in real-time and make informed decisions without needing to physically visit the site. Another business uses it to manage smart home devices, ensuring their customers have seamless control over their homes from anywhere in the world.
Cost Considerations
One of the biggest concerns when adopting new technology is cost. Fortunately, AWS offers a pay-as-you-go model, which means you only pay for the resources you use. However, it’s important to monitor your usage closely to avoid unexpected charges. AWS also provides a free tier for new users, which is perfect for testing and small-scale projects.
Future Trends in RemoteIoT SSH
As technology continues to evolve, so does the landscape of RemoteIoT SSH AWS Example. Expect to see advancements in areas like quantum encryption, edge computing, and AI-driven automation. These innovations will further enhance the security and efficiency of IoT setups, making them even more accessible and powerful.
So, what does the future hold? Well, imagine a world where your IoT devices are not only secure but also self-healing, capable of detecting and fixing issues on their own. That’s the kind of future we’re heading towards, and AWS is leading the charge.
Conclusion
And there you have it—your ultimate guide to RemoteIoT SSH AWS Example. By now, you should have a solid understanding of what it is, why it’s important, and how to set it up. Remember, security is key, and leveraging AWS for your IoT needs is a smart move that will pay off in the long run.
So, what are you waiting for? Start exploring RemoteIoT SSH AWS Example today and take your IoT management to the next level. Don’t forget to leave a comment below with your thoughts or questions, and share this article with your tech-savvy friends. Together, let’s build a more connected and secure future!